By now, nearly everyone who works in an office has heard of phishing attacks: Someone pretending to be someone you know emails you and attempts to trick you into giving them sensitive information. While phishing attacks are pretty common, how much do you know about smishing?
Smishing is similar to phishing, except that the fake messages come to your cellphone in the form of texts instead of to your email. Keep an eye out for these four smishing attacks you might see in 2021.
If you need to ensure your employees’ mobile devices are secure, check out our MDM/BYOD Product Selection Tool and get a short, unbiased list of vendors that can help.
Table of contents
- 4 types of smishing attacks
- “Urgent” messages about your credit card or bank account
- Notifications that you’ve won something
- Fake survey links
- Fake messages from trusted brands
- How to spot smishing
- Tools that can prevent smishing attacks
4 types of smishing attacks
Smishing attacks can take on many forms, but these four are some of the most common you’ll run into.
1. “Urgent” messages about your credit card or bank account
Many hackers will send text messages posing as your bank or credit card company to get you to click on a link or provide them with sensitive information. They may tell you that your account has been locked and offer a link to rectify it or make up a fraudulent purchase and ask you to verify your identity to remove it.
While banks and credit card companies do occasionally send text to their members, it’s usually for authentication codes, or you might get an alert that there’s been a suspicious purchase on your account. However, these legitimate messages will almost never include links.
2. Fake messages from trusted brands
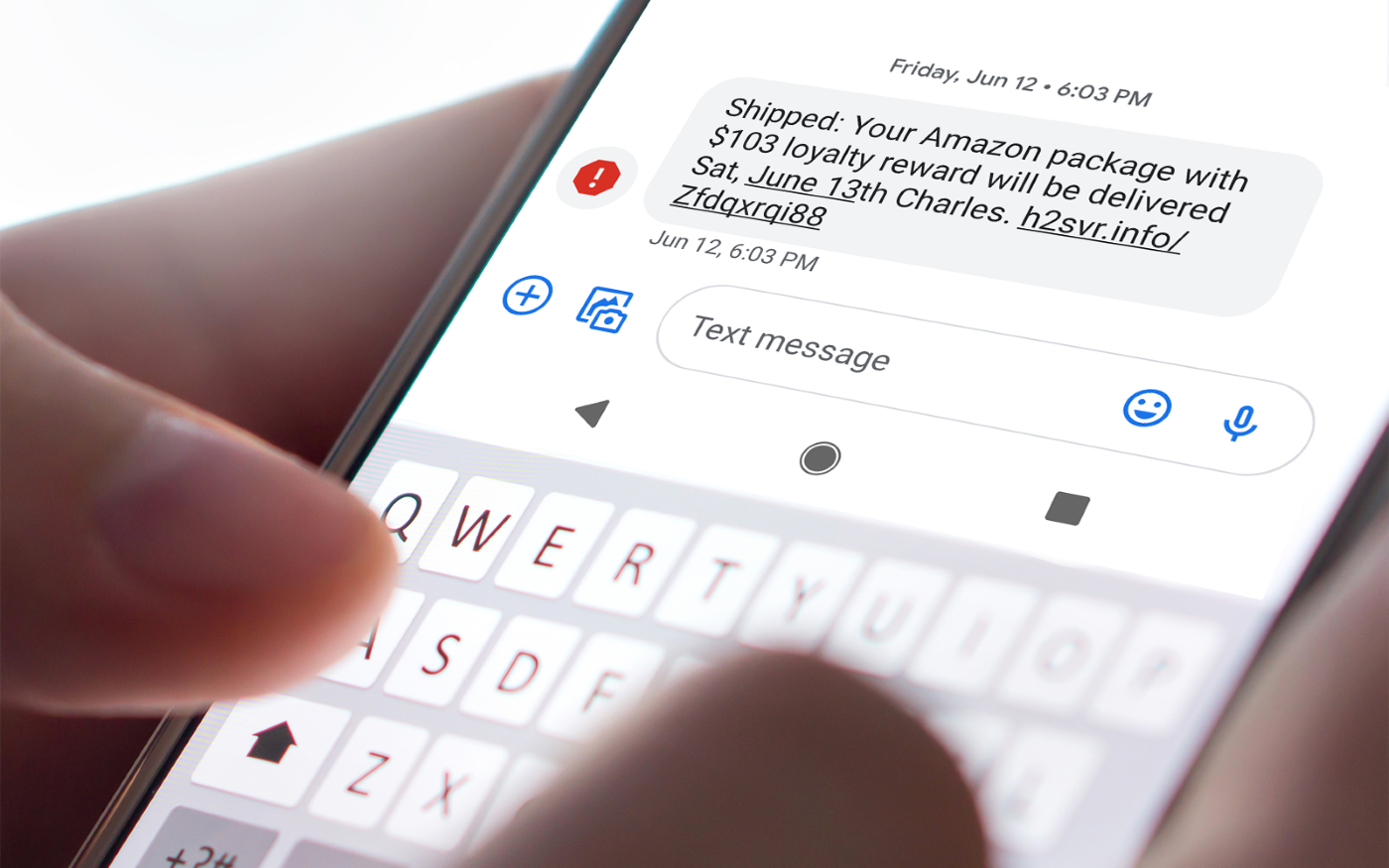
Because brands want to paint themselves as helpful, more companies are starting to send out notifications for shipping or when there is strange activity on their customers’ accounts. Whether it was a login from a new device or a purchase from a different city, businesses want their customers to feel like their data is safe with them. While this is helpful in many ways, it also makes it easier for smishers to use this tactic to blend in.
Also read: Cybersecurity Trends in 2020: BYOD and Mobile
3. Fake survey links
Fake survey links are a bit tough because most people don’t actually want to take surveys, so even the legitimate ones are usually unsolicited. One indicator of a real survey is that it was prompted by something you did. Maybe you went to a store or had an interaction with a customer service team. Additionally, more survey tools are now allowing you to put your answer right in the text message rather than having to navigate to a website.
4. Notifications you’ve won something
Sometimes, you’ll get text messages claiming you’ve won something, and you need to click on a link to claim your prize. While this sounds great, it’s easy to see through these scams. For one, if you didn’t enter for anything, you definitely didn’t win it. Second, links are too easy to share. If all someone really had to do to win a prize was click on a link, people would share them, so their friends could get the prize, too.
How to spot smishing

Smishing attacks, like phishing attacks, are looking for the easiest targets, so they’re fairly easy to spot if you’re wary. Bad grammar and misspelled words are good indicators you’re dealing with a smishing attack. Additionally, links included in spam messages will often be slightly altered from the site the text says you’re going to, for example, ama.zon.com vs. amazon.com.
If you’re not sure about a message, you can also do an internet search for the number and the message. If it’s smishing, you probably aren’t the only one who’s gotten the exact same text.
While you can’t stop people from smishing, you can at least ensure that you don’t fall victim to it. If a text message contains a link and it doesn’t come from someone you recognize or you aren’t sure it’s really them, don’t click on that link.
If you think a text message has come from a company you trust, you should always verify it before clicking on any links. Look up the company’s customer service line on Google and give them a call. If they did contact you, they’ll have a record of it. Just like email addresses, phone numbers can be spoofed, so it’s always better to verify. There are also tools you can use to prevent smishing in the first place.
Tools that can prevent smishing attacks
Many smishers use location data to generate local numbers and make their attacks seem more legitimate. Adding a VPN to your phone can spoof your location and make it seem like you’re located in another part of the country. When you get messages related to your spoofed location, you can be confident that they’re fake. Pulse Secure offers a variety of security tools, including VPNs to keep your devices safer.
[get-pricing category=”CRM” cta=”Get Pricing” width=”200px” url=”pulse-secure-reviews”][/get-pricing]
Spam blocking apps are also great ways to prevent smishing. Your phone’s operating system might come with one, but you might also need to search through the app store to find one that’s a little more robust. Robo Shield is a great option for iPhone users and Truecaller works well for Android users.
As a company, mobile device management (MDM) software is a great tool to keep your data safe even while your employees are working remotely. MDM platforms offer device security, encrypted messaging platforms, and remote access for security and IT support purposes. Options like Hexnode let you manage devices from a single point of control and lock or wipe a device remotely to keep it secure.
[get-pricing category=”CRM” cta=”Get Pricing” width=”200px” url=”hexnode-reviews”][/get-pricing]
If mobile device management seems like the right call for your company, check out our MDM/BYOD Product Selection Tool and Guide. After answering a short survey, our team will provide a short, unbiased list of products that will meet your business’s needs.
