Written by
Aron Vaughan, Staff Writer
Read more by Aron →
Reviewed by
Corey Noles, Editor
What is attack surface management?
Attack Surface Management (ASM) is a cybersecurity strategy aiming to identify, assess, and secure all external digital assets accessible from the internet. In a world where digital footprints expand daily, ASM monitors and mitigates the risks associated with these evolving attack vectors. By continuously identifying exposed data, unsecured servers, misconfigured cloud services, and other vulnerabilities, it minimizes the ‘surface’ that attackers can exploit. ASM solutions also help organizations adhere to security compliance regulations. This proactive approach is crucial in today’s digital landscape to safeguard the integrity, confidentiality, and availability of an organization’s information systems. Remember, in cybersecurity, your defenses are only as strong as your weakest point; ASM ensures there are as few weak points as possible.
Based on our evaluation of 20 titles, the best IT attack surface management software solutions are:
- UpGuard: Best for third-party risk management
- CrowdStrike Falcon Service: Best for endpoint protection
- CyCognito: Best for automated asset discovery
- Mandiant Advantage: Best for threat intelligence and response
- ManageEngine Vulnerability Manager: Best for small to mid-sized businesses seeking affordable vulnerability management
- Microsoft Defender External Attack Surface Management: Best for Microsoft ecosystem integration
Our picks for the best attack surface management software
UpGuard – Best for third-party risk management

Pros
Cons
UpGuard is an Attack Surface Management tool offering an impressive suite of features—most notably, its third-party risk management, which provides continuous monitoring and detailed, actionable reports on vendor security postures. Its automated risk assessment yields clear, digestible data, aiding effective decision-making. User-friendly despite its robustness, UpGuard also offers breach detection services, constantly scanning for exposed data. Its standout offering is the Cyber Risk Score, giving you an instant, quantifiable view of your cybersecurity health. Though mighty, UpGuard retains an approachable feel, making it a reliable choice for businesses aiming to secure their digital environments.
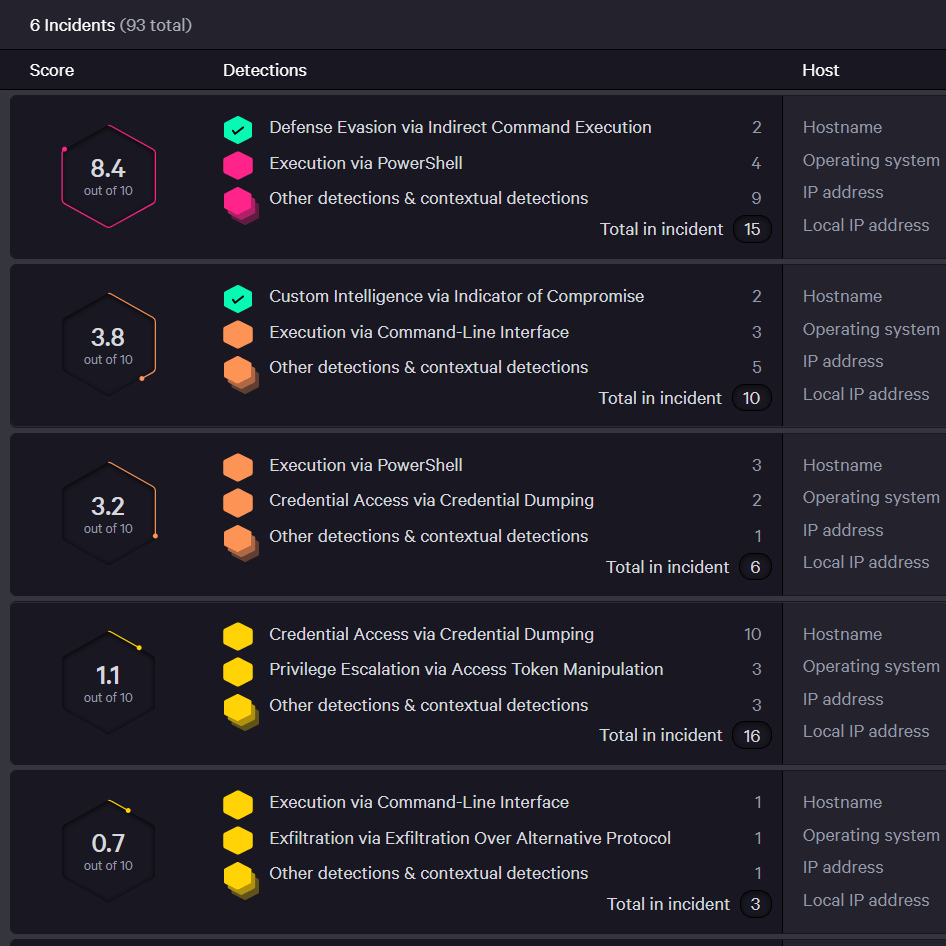
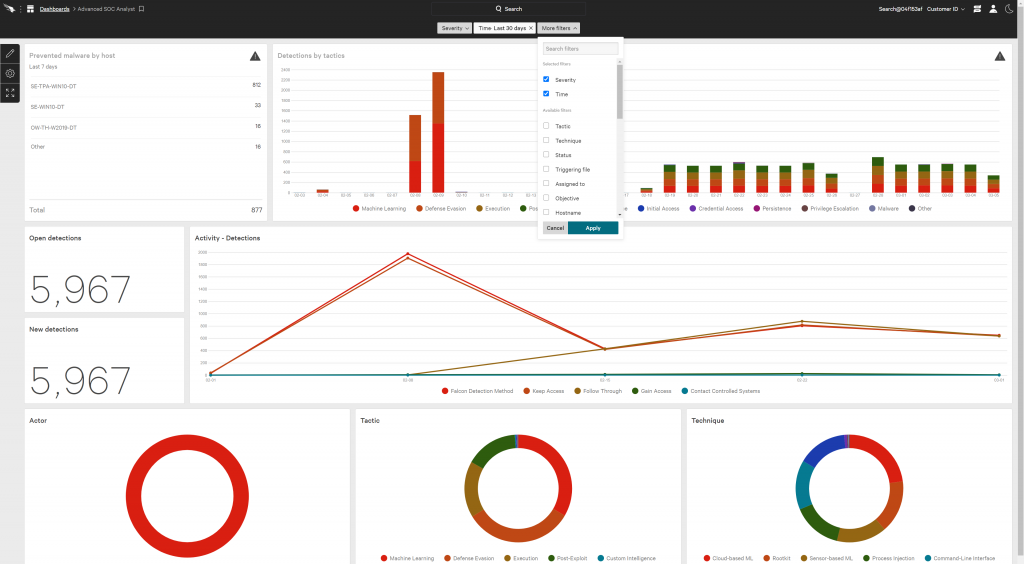
CrowdStrike Falcon Service – Best for endpoint protection

Pros
Cons
CrowdStrike Falcon Service is a comprehensive, cloud-native cybersecurity solution specializing in endpoint protection. It offers robust defense through AI-enabled next-gen antivirus, real-time endpoint detection, and threat intelligence. Its standout feature, Falcon OverWatch, provides managed threat hunting, offering an extra layer of proactive protection. Despite its extensive capabilities, CrowdStrike remains efficient, minimizing system impact thanks to its single agent architecture. While its advanced features demand a learning curve, it’s a worthwhile trade-off for the comprehensive protection and insight CrowdStrike provides, particularly for businesses with significant endpoint security needs.
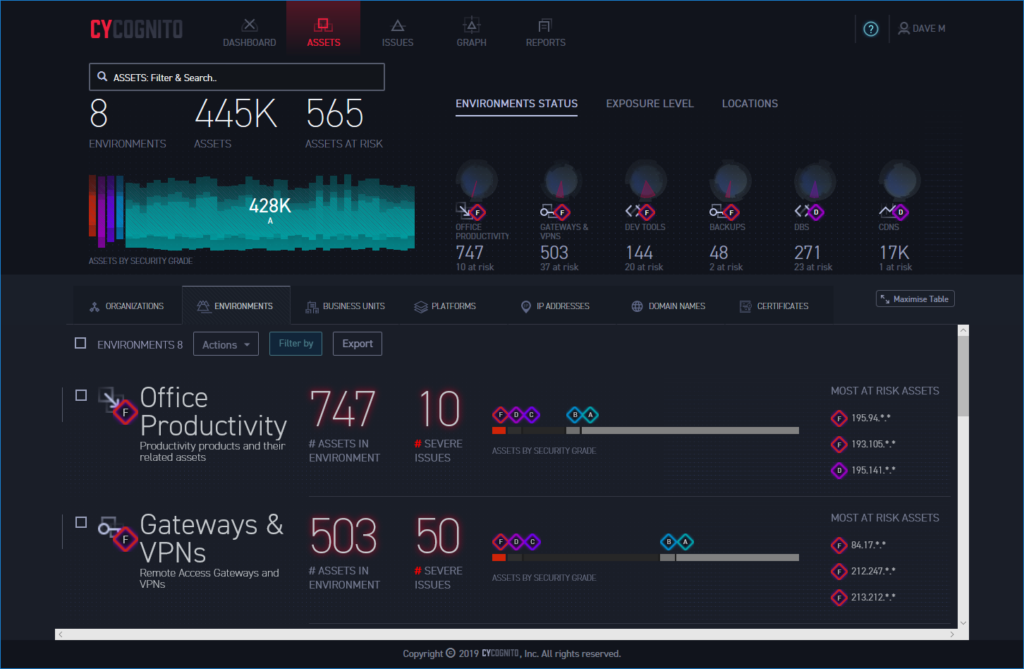
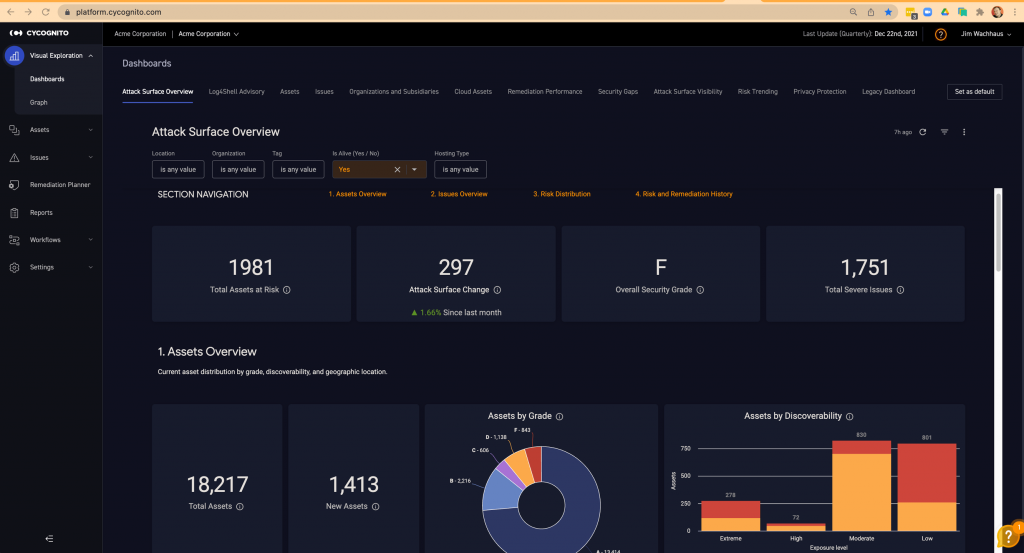
CyCognito – Best for automated asset discovery

Pros
Cons
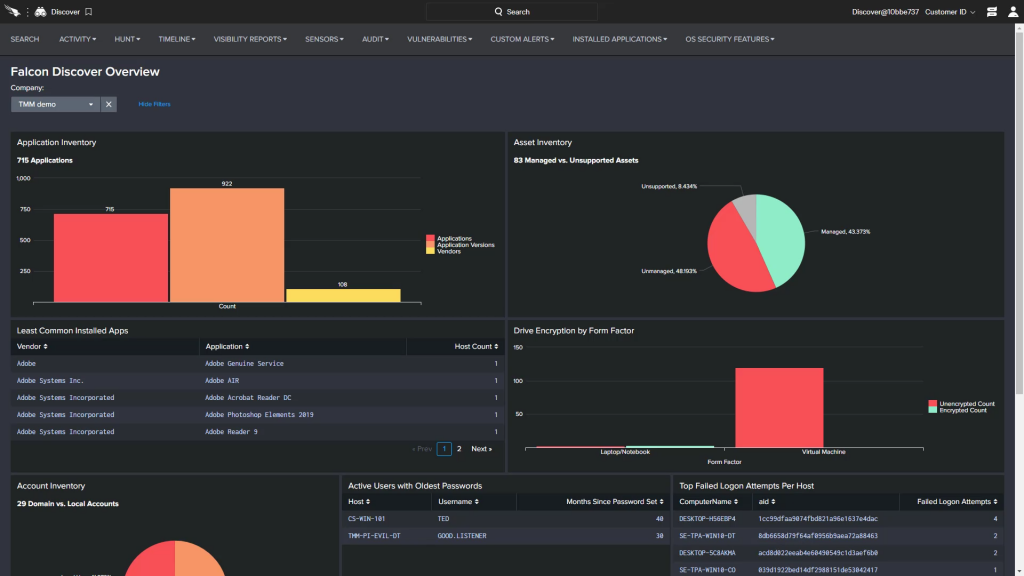
CyCognito is a sophisticated, bot-driven cybersecurity platform that employs a hacker’s approach to identify, assess, and prioritize risks in an organization’s digital infrastructure. Continuously scanning the full expanse of an organization’s digital assets, including IoT devices, cloud-based infrastructure, and third-party assets, it illuminates hidden vulnerabilities, offers a ranking of threats, and provides actionable insights. It’s an uncomplicated and flexible solution, requiring no setup or advanced knowledge, serving comprehensive reports that articulate network health and vulnerability management to both technical and non-technical audiences, making it an essential tool in the realm of cybersecurity.
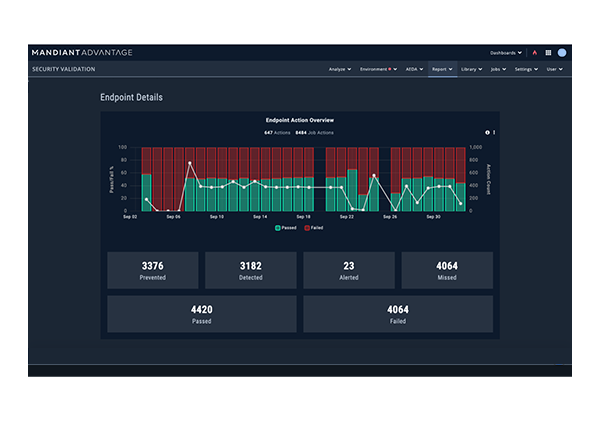
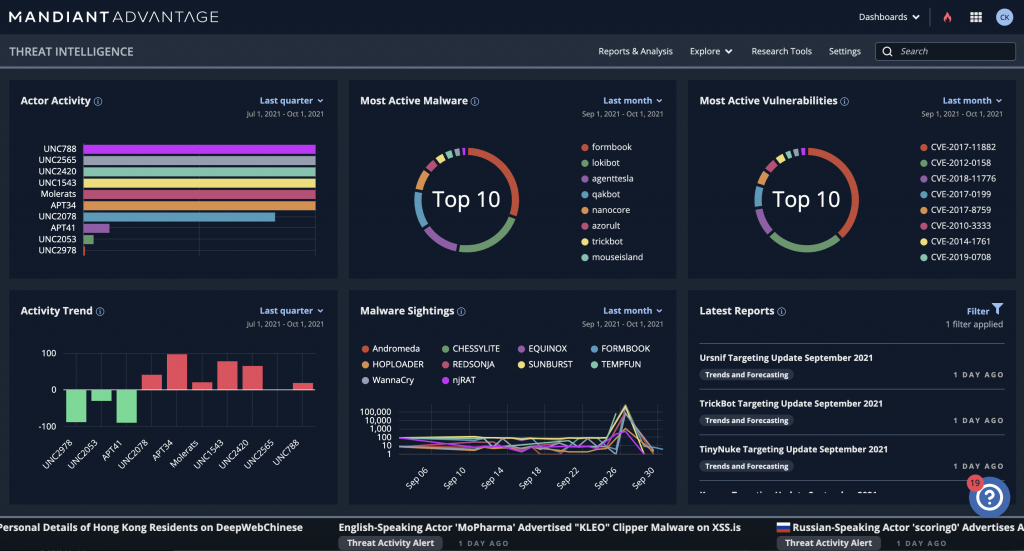
Mandiant Advantage – Best for threat intelligence and response

Pros
Cons
Mandiant Advantage is a formidable Automated Security Management (ASM) solution that provides a unified, intelligence-led approach to security. This platform ensures comprehensive visibility over your digital assets, bolstered by real-time threat intelligence and automated threat prioritization. It is acclaimed for its sophisticated AI-driven analysis and Incident Response capabilities. Its Threat Intelligence Library offers deep insights into threat actors, techniques, and preventative measures. Mandiant Advantage empowers organizations with a robust defense strategy, enabling them to anticipate, prioritize, and effectively respond to threats, thereby fortifying their security posture across diverse digital environments.
ManageEngine Vulnerability Manager – Best for small to mid-sized businesses

Pros
Cons
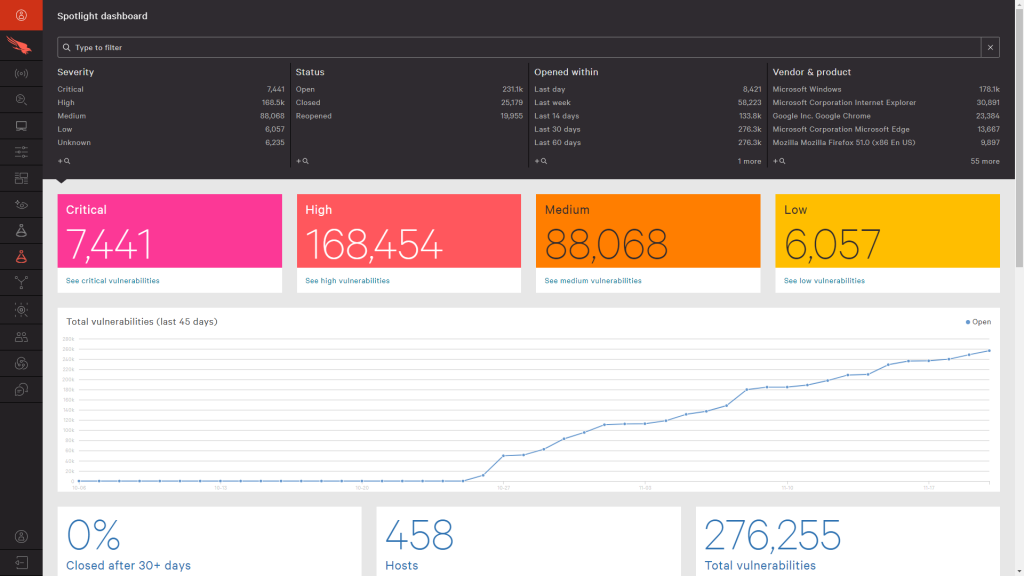
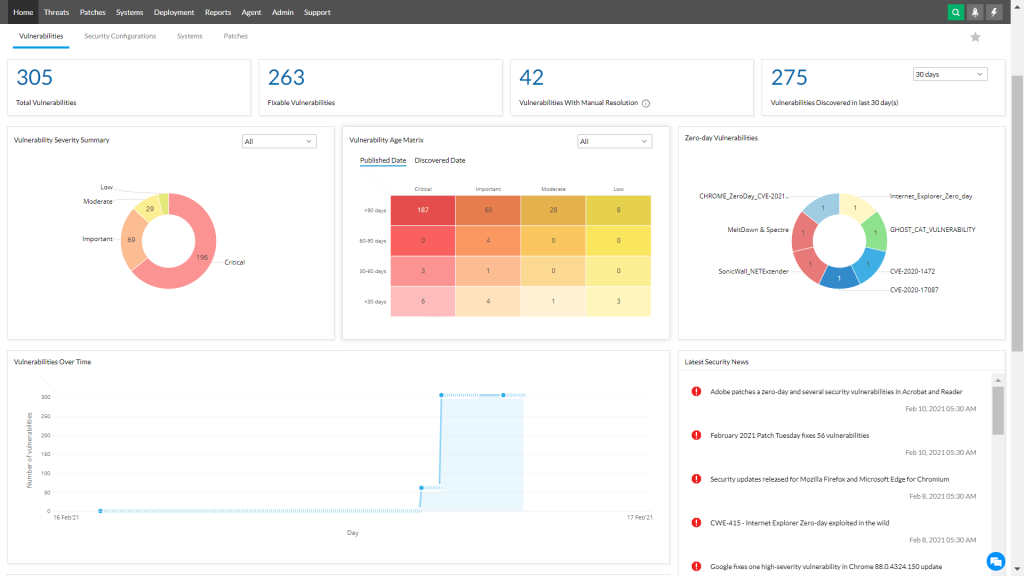
ManageEngine Vulnerability Manager is a robust cybersecurity solution designed to assist businesses in identifying and remediating vulnerabilities in their IT infrastructure. The tool performs comprehensive vulnerability scanning across network devices, servers, web applications, and databases, enabling organizations to keep their security posture updated. The solution provides detailed vulnerability reports, risk scoring, and actionable remediation advice, helping teams prioritize and address issues effectively. In addition, it features automated patch management to reduce manual effort. Its non-intrusive scanning ensures minimal disruption to regular business operations. ManageEngine Vulnerability Manager’s capabilities, combined with its user-friendly interface and competitive pricing, make it an attractive option for businesses of all sizes, especially small to midsize organizations.
Microsoft Defender External Attack Surface Management – Best for Microsoft ecosystem integration

Pros
Cons
Rooted in the widely used Microsoft ecosystem, Defender External Attack Surface Management facilitates threat detection, vulnerability assessment, and remediation processes. With a focus on external-facing assets, it provides actionable insights for enhancing security posture. Its strengths lie in its integration with Microsoft’s extensive security services, automated threat intelligence and response, and cost-effectiveness, making it a suitable choice for businesses seeking a robust, affordable, and user-friendly solution to manage their external attack surface.
Finding your new attack surface management software
Understanding the Components of an Attack Surface
Physical components
Physical components include any hardware that can be physically accessed or manipulated to gain unauthorized entry into a system. This includes servers, laptops, smartphones, routers, and IoT devices. Ensuring physical security is a fundamental part of ASM.
Digital components
Digital components of an attack surface are the software or digital systems, including operating systems, applications, databases, and networks, that can be exploited. A large digital attack surface may pose a higher risk due to the potential for software bugs, misconfigurations, and unpatched vulnerabilities.
Human components
Humans represent the third pillar of an attack surface. This includes employees, contractors, or any individual with access to your systems. Human error, negligence, or malicious intent can introduce serious vulnerabilities, making education and awareness key elements in managing this aspect of the attack surface.
Add an extra layer of security to your network with Zero Trust software.
Key challenges in attack surface management
Growing complexity of networks
As businesses adopt new technologies, their attack surfaces expand and become more complex. This includes a rise in the use of cloud services, IoT devices, and mobile technologies, which can create additional entry points for attackers.
Rapidly evolving threat landscape
Cyber threats are constantly evolving, with new vulnerabilities and attack vectors emerging regularly. This makes the task of managing and securing an organization’s attack surface an ongoing challenge.
Managing unknown assets
A significant challenge in ASM is the management of unknown or unmanaged assets. These can range from forgotten servers to third-party applications, which often slip under the radar and provide potential footholds for attackers.
Best practices for effective attack surface management
Regular asset discovery and management
Continuous identification and tracking of assets is crucial for effective ASM. Regular inventory checks, network mapping, and automated discovery tools can help keep track of all components in your attack surface.
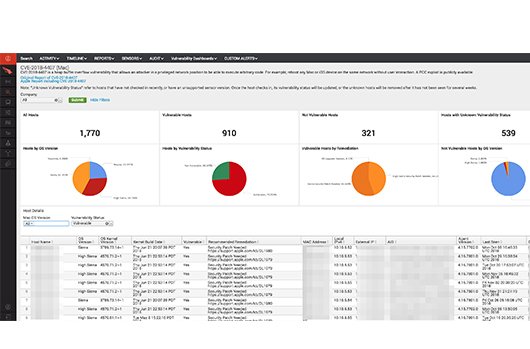
Continuous vulnerability assessments
Regularly scanning for vulnerabilities helps identify weaknesses that could be exploited by attackers. Employing continuous vulnerability assessment tools provides a more proactive and dynamic approach to threat management.
Prioritization of remediation efforts
Not all vulnerabilities pose the same risk. Prioritizing remediation efforts based on the potential impact and ease of exploitability of vulnerabilities helps optimize resource allocation and reduce risk faster.
Employee training and awareness
People are often the weakest link in security. Regular cybersecurity training and awareness programs can significantly reduce the risk of human-induced security incidents and enhance your overall security posture.
ALSO READ: Best Security Information and Event Management (SIEM) Software Guide
Finding the right attack surface management software for your business
Choosing the right Attack Surface Management (ASM) software is critical to achieving a robust cybersecurity posture. Your ideal tool should align with your network’s structure, your operational needs, and your risk profile. It should offer continuous visibility over all your assets—physical, digital, and human—while also being proactive in identifying and assessing vulnerabilities. But, remember, no single solution is a magic bullet. Your organization’s security ultimately depends on an integrated, layered strategy that combines robust ASM with continuous monitoring, regular staff training, and a proactive culture of cybersecurity awareness. Find the software that complements your strategy and empowers your defense, and you’ll be well on your way to a more secure future.
Choosing the best software for attack surface management
Ready to start your surface attack management comparison? Our Technology Advisors are here to help you find the perfect tool for your company’s projects. Call for a free 5-minute consultation, or complete the form at the bottom of this page for fast, free recommendations based on your needs.